You’ve likely experienced a cyber attack at some point during your career or personal life. For example, you may have had an account hacked into or received an alarming message from a service provider that there has been a systems data breach and your personal details were compromised. With larger-scale cyberattacks, these often go unnoticed or unreported for months on end, leaving the end-users completely unaware of what has transpired.
You may be wondering just how secure your data really is when you sign-up for a new loyalty program, give your personal details to have a credit check run, or sign supplier contracts on behalf of your organization.
Penetration testing (pen testing) plays an integral role in ensuring client data security. In this post, we’ll explain why pen testing is important, how it works, and why we use it on the Traxo platform to improve security for our clients.
Definition of Penetration Testing
In summary, Penetration Testing is a simulated, ethical cyberattack against a business to identify areas of weakness in the data infrastructure, evaluate the information security effectiveness, and determine security controls and response times. If your business was to get hacked tomorrow, how long would it take for you to be made aware of the incident and react to fix the problem at hand? That’s essentially what pen testing seeks to answer.
Why is Pen Testing Important?
The goal is to find the vulnerabilities before real-world criminal hackers do so that internal security teams can mitigate any potential risks in their information technology (IT) infrastructure, before becoming a victim of a major cyberattack. Undergoing pen testing is an important first step to ensuring client data is safe and secure. This proactive approach allows businesses to undergo a stress test and course correct any weaknesses in both infrastructures and the businesses response protocol.
Consider Pen Testing in your next RFQ
As data security continues to be top of mind for travel managers and individuals alike, you may consider asking suppliers if they have undergone PEN Testing during your next RFQ or RFP. If they have, ask how recently and if the pen testing was outsourced to a third party specialized in pen testing. Upon request, they should be able to provide you with documentation with these details in a report from their testing vendor. These inquiries will let your prospective suppliers know that you take data security seriously and that you are interested in working with companies that protect their customers' data in a proactive approach.
What is Traxo doing to keep our customers' data safe?
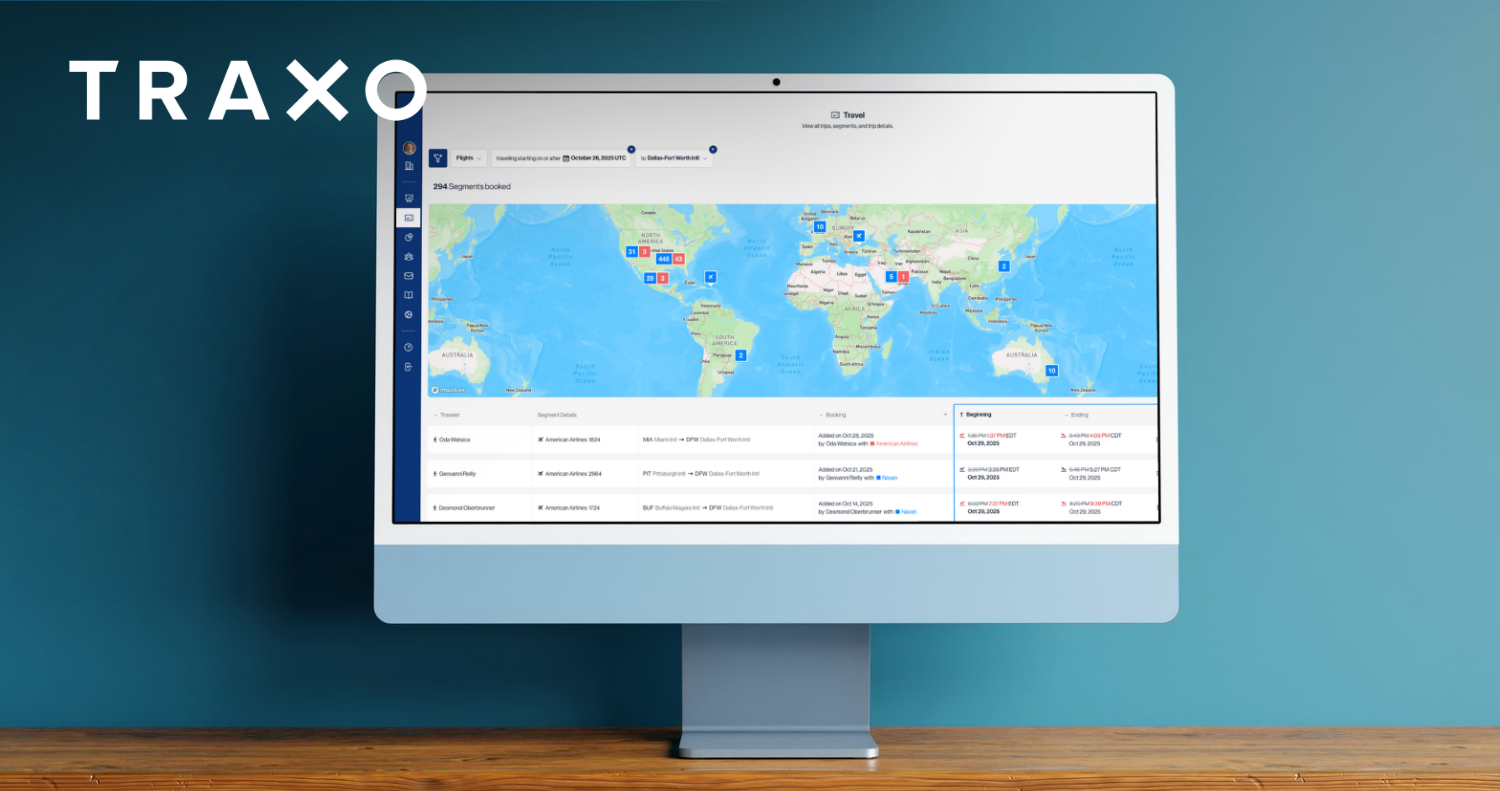
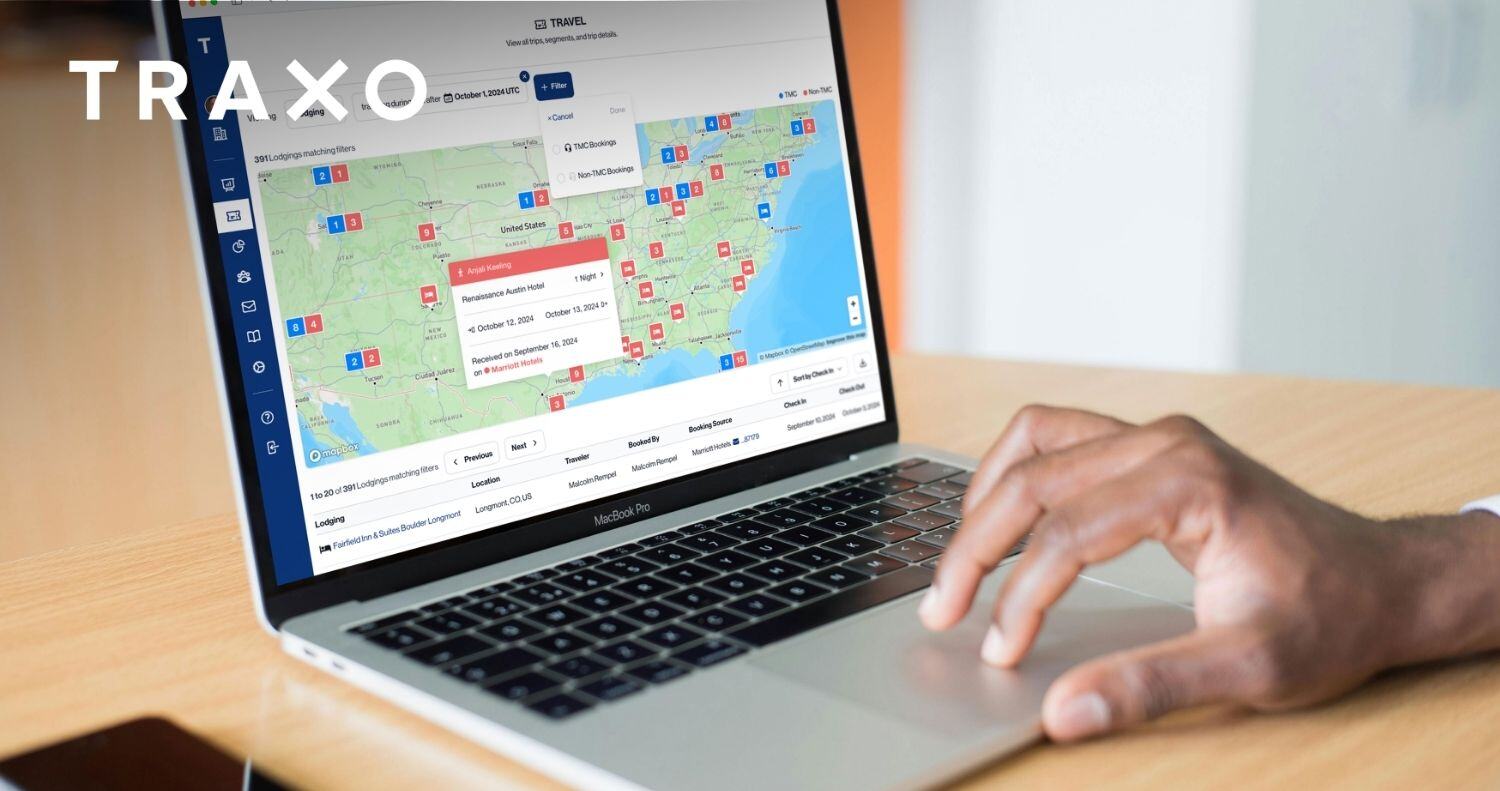
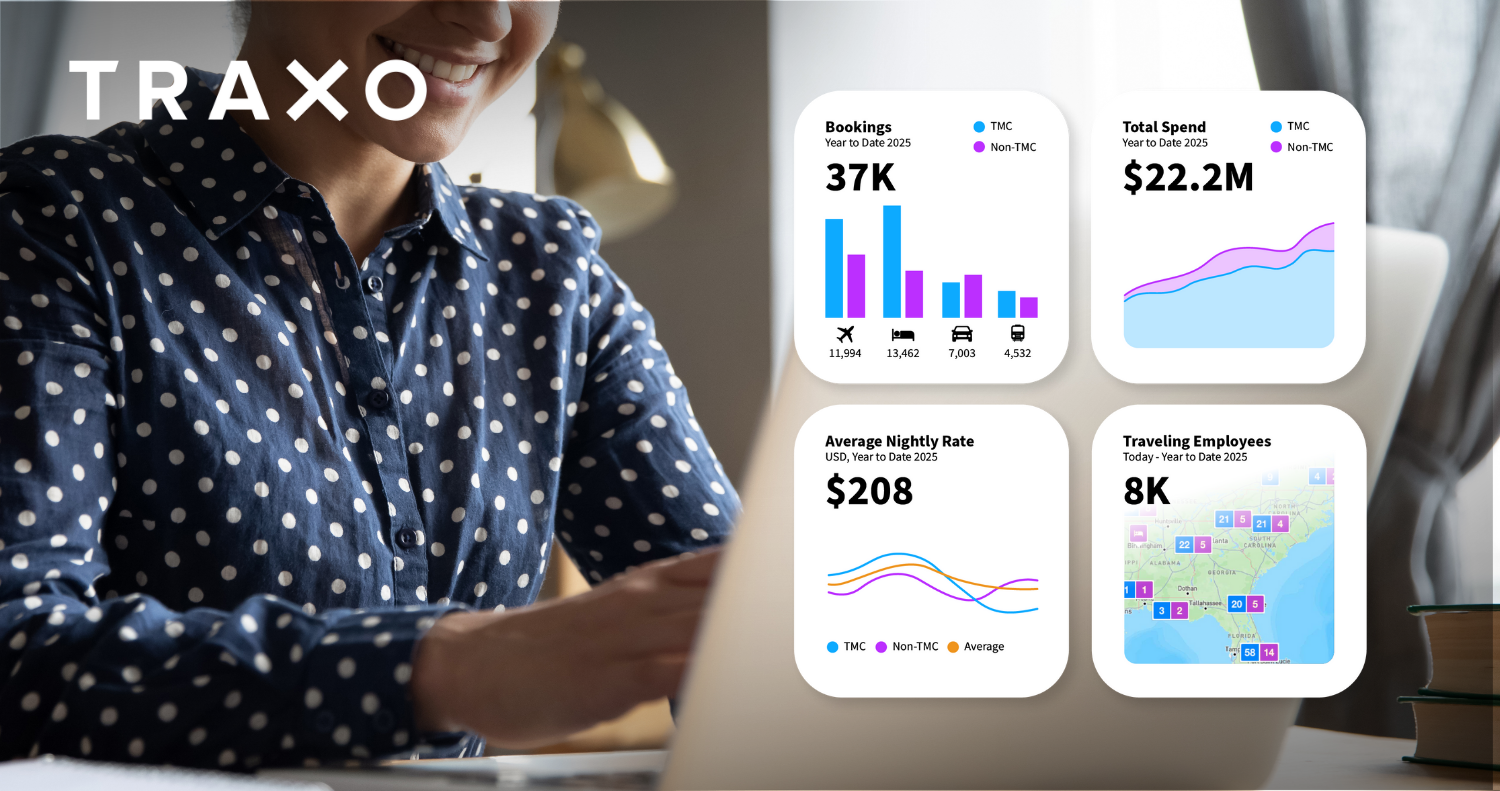
At Traxo, we believe organizations should have easy access to all employee travel data. Along with providing easy access, we’re constantly working to ensure your employee travel data is only made available to you or the service providers you trust—no one else.
That’s why Traxo proactively underwent pen testing to ensure our customers' peace of mind, knowing their data is secure within our network. Through this effort, we have identified and addressed potential vulnerabilities in our system to circumvent any future criminal hacking attempts on our network. Our customers' data security is always at the forefront, and we invest both time and money to ensure our security is untouchable on an ongoing basis.
For our Traxo customers or prospects, a copy of our Penetration Testing results can be requested through the operational security section of the Traxo security page.





.png)

.jpg)

.jpg)



























.png)









